IP and HTTP permissions
In IP and HTTP method configuration you can configure which IP addresses are allowed to access an author or public instance. If an IP that is not configured attempts to access the instance, it will be denied access.
The filtering also verifies the HTTP methods that the IP can use when accessing the instance. If an allowed IP attempts to access the instance using a HTTP method that is not configured, it will be denied access.
IP and HTTP method configuration is in Configuration >
/server/IPConfig.
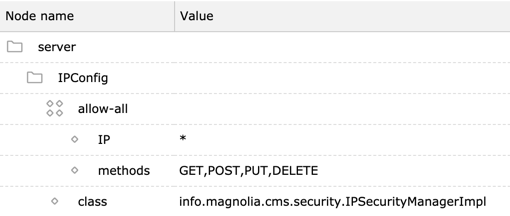
In the example above, allow-all is a rule. You can add any number of
rules under /server/IPConfig. Each rule must have IP and methods
properties.
The IP property’s value can be:
-
The
*wildcard character, meaning any IP address is allowed. -
A single IP address, for example
192.168.100.0. -
A block of IP addresses described using the CIDR (slash) notation, for example
192.168.100.0/22, representing the 1024 IPv4 addresses from 192.168.100.0 to 192.168.103.255.
The methods property can be set to multiple HTTP methods separated by commas. Any
valid HTTP method can
be included in the list.
To create a rule:
-
Add a content node in Configuration >
/server/IPConfig. -
Add
IPandmethodsproperties. -
Set the value of the
IPproperty. -
Set the value of the
methodsproperty to HTTP methods (single or separated by commas).
The default setting allows all IPs to access the instance using GET, POST, PUT and DELETE methods. You can also allow HEAD methods. HEAD, PUT and DELETE methods are typically used by services such as the WebDAV or REST modules. This makes is possible to use other tools to edit content on the author instance or to integrate other applications on the public instance.